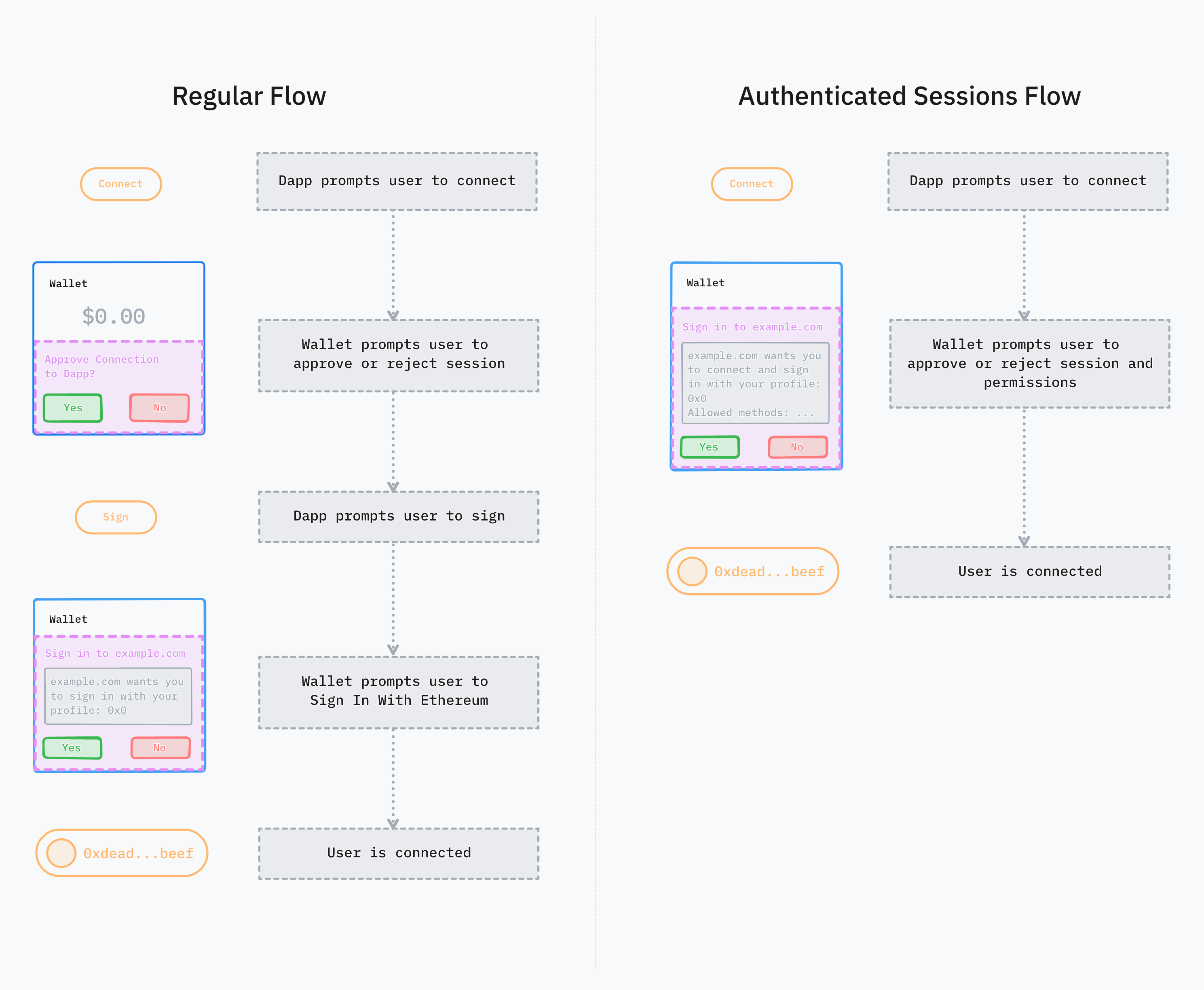
// Approach 1
// Sign the authentication message(s) to create a verifiable authentication object(s)
final credentials = EthPrivateKey.fromHex('$privateKey');
final signature = credentials.signPersonalMessageToUint8List(
Uint8List.fromList(message.codeUnits),
);
final hexSignature = bytesToHex(signature, include0x: true);
// Build the authentication object(s)
final cacao = AuthSignature.buildAuthObject(
requestPayload: cacaoRequestPayload,
signature: CacaoSignature(
t: CacaoSignature.EIP191,
s: hexSignature,
),
iss: iss,
);
// Approve
await _walletKit!.approveSessionAuthenticate(
id: args.id,
auths: [cacao],
);
// Approach 2
// Note that you can also sign multiple messages for every requested chain/address pair
final List<Cacao> cacaos = [];
for (var chain in newAuthPayload.chains) {
final message = _walletKit!.formatAuthMessage(
iss: iss,
cacaoPayload: cacaoRequestPayload,
);
final credentials = EthPrivateKey.fromHex('$privateKey');
final signature = credentials.signPersonalMessageToUint8List(
Uint8List.fromList(message.codeUnits),
);
final hexSignature = bytesToHex(signature, include0x: true);
final cacao = AuthSignature.buildAuthObject(
requestPayload: cacaoRequestPayload,
signature: CacaoSignature(
t: CacaoSignature.EIP191,
s: hexSignature,
),
iss: iss,
);
cacaos.add(cacao)
}
// Approve
await _walletKit!.approveSessionAuthenticate(
id: args.id,
auths: cacaos,
);